Protecting Private Web Content from Embedded Scripts
Thursday, June 16th, 2011Our paper on protecting private web content from embedded scripts is now available:
Yuchen Zhou and David Evans. Protecting Private Web Content from Embedded Scripts. European Symposium on Research in Computer Security (ESORICS 2011). Lueven, Belguim. 12-14 September 2011. [PDF, 20 pages]
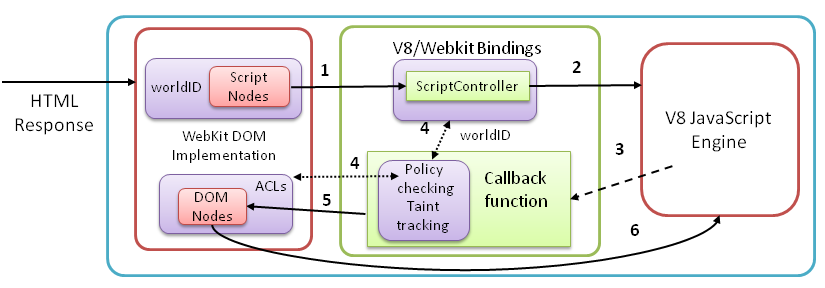
The paper addresses the problem of when web pages embed scripts from third parties (such as advertising networks or analytics tools) in their pages that contain user’s personal content. Since many such scripts must be embedded directly (that is, not in a separate iframe), they have access to the full page DOM and can access and manipulate this data. Our solution adopts the isolated worlds mechanism to isolate embedded scripts and provide a policy-limited access model. We also present a technique for automatically learning which nodes in a web page may contain sensitive data that should be protected from third-party scripts.
Yuchen will present the paper at ESORICS in Belgium in September.
Source Code
Modified Chromium: https://github.com/Treeeater/Chromium_on_windows
Policy Learner Proxy: https://github.com/Treeeater/GreasySpoon-proxy-script


